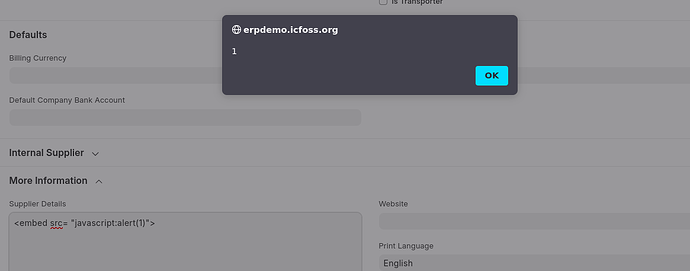
Dear colleagues,
I would like to share here some configuration options that can be applied to the nginx web server configuration (./config/nginx.conf) to help improve the security of your ERPNext server. This applies for self-hosted ERPNext servers.
For each server { ... } block, these options can be added
# don't send the nginx version number in error pages and server header
server_tokens off;
# config to enable HSTS (HTTP Strict Transport Security)
add_header Strict-Transport-Security "max-age=63072000; includeSubdomains;";
# protect against cross-site attacks
add_header X-Frame-Options "SAMEORIGIN";
# This header enables the Cross-site scripting (XSS) filter built into most recent web browsers.
add_header X-XSS-Protection "1; mode=block";
# when serving user-supplied content, include a X-Content-Type-Options: nosniff header along with the Content-Type: header,
# to disable content-type sniffing on some browsers.
add_header X-Content-Type-Options nosniff;
# with Content Security Policy (CSP) enabled (and a browser that supports it),
# you can tell the browser that it can only download content from the domains you explicitly allow
add_header Content-Security-Policy "default-src 'self' https://cdn.rawgit.com/frappe/emoji/master/emoji https://raw.githubusercontent.com/frappe/emoji/master/emoji; script-src 'self' 'unsafe-inline' 'unsafe-eval' https://www.google-analytics.com; img-src 'self' https://www.google-analytics.com data:; style-src 'self' 'unsafe-inline'; font-src 'self'; frame-src 'self'; object-src 'none'";
After saving changes, make sure to run
$ sudo service nginx reload
In some cases, the CSP might be rather strict (observe possible errors in your browser console).
Thanks to login_denied for his support in this matter. Any feedback is appreciated!