Hi Team,
We have identified a serious security vulnerability in the Frappe login mechanism that needs immediate attention and a fix from the framework maintainers.
 Issue Summary:
Issue Summary:
- The login form (
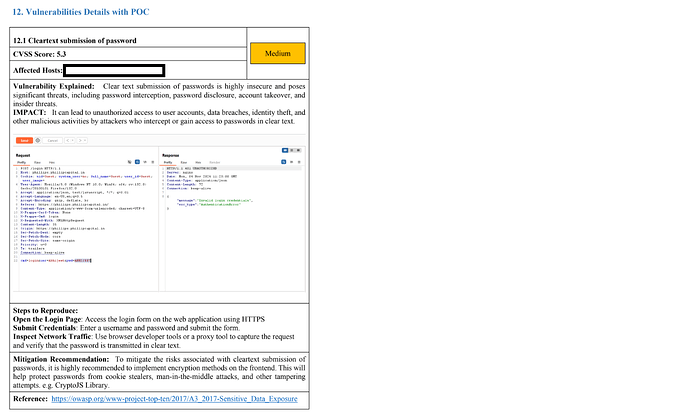
/login) sends the password (args.pwd) in cleartext in the body of aPOSTrequest. - Even though HTTPS is enabled, this behavior was flagged by a security audit as Sensitive Data Exposure (OWASP A3:2017) with a CVSS Score of 5.3.
- The vulnerability was confirmed via tools like Burp Suite which showed the password being sent in plain text from the browser.
 Impact:
Impact:
This can lead to:
- Password interception by malicious browser plugins, compromised endpoints, or internal network actors.
- Non-compliance with common security standards that require encrypted or obfuscated password transmission.
- Exposure in memory dumps, browser DevTools, or intermediary proxies.
 Proof of Concept (POC):
Proof of Concept (POC):
Please refer to the attached screenshot from our security assessment report which clearly shows the password submitted in plaintext.
 Request for Frappe Team:
Request for Frappe Team:
- Is this behavior known or acknowledged by the framework team?
- Is there an official fix or patch planned?
- How should this issue be mitigated properly without forking core logic?
We’re looking for a framework-level fix or a best practice from the maintainers
 Environment:
Environment:
- Frappe Version: v15
- Deployment: Linux
- Affected Hosts: [Redacted in public post]
This vulnerability has failed our internal security audit and needs urgent resolution. Please advise on how this can be handled going forward.
Thanks in advance!