Hi, I am trying to authenticate ERPNext users using Keycloak IdP.
I configured it as shown here: oAuth client login button - #6 by revant_one
and it seems almost to be done, still, I get the error:
frappe.exceptions.ValidationError: Email not verified with Keycloak
although it is actually verified.
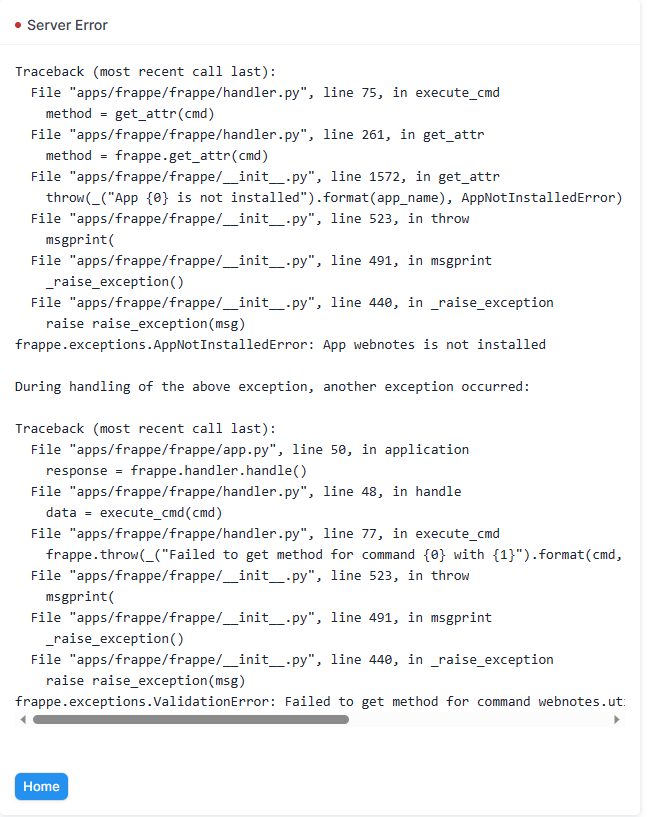
Server Error
Traceback (most recent call last):
File "apps/frappe/frappe/app.py", line 66, in application
response = frappe.api.handle()
File "apps/frappe/frappe/api.py", line 54, in handle
return frappe.handler.handle()
File "apps/frappe/frappe/handler.py", line 45, in handle
data = execute_cmd(cmd)
File "apps/frappe/frappe/handler.py", line 83, in execute_cmd
return frappe.call(method, **frappe.form_dict)
File "apps/frappe/frappe/__init__.py", line 1607, in call
return fn(*args, **newargs)
File "apps/frappe/frappe/integrations/oauth2_logins.py", line 58, in custom
login_via_oauth2(provider, code, state, decoder=decoder_compat)
File "apps/frappe/frappe/utils/oauth.py", line 115, in login_via_oauth2
info = get_info_via_oauth(provider, code, decoder)
File "apps/frappe/frappe/utils/oauth.py", line 161, in get_info_via_oauth
frappe.throw(_("Email not verified with {0}").format(provider.title()))
File "apps/frappe/frappe/__init__.py", line 525, in throw
msgprint(
File "apps/frappe/frappe/__init__.py", line 493, in msgprint
_raise_exception()
File "apps/frappe/frappe/__init__.py", line 442, in _raise_exception
raise raise_exception(msg)
frappe.exceptions.ValidationError: Email not verified with Keycloak
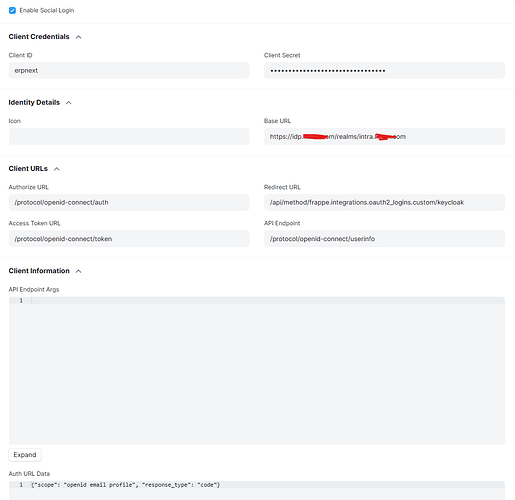
Here is again my configuration:
Here is a small confirmation that the user I am using for logging in in Keycloak has a verified email:
![]()
Is it a bug? What could be wrong?